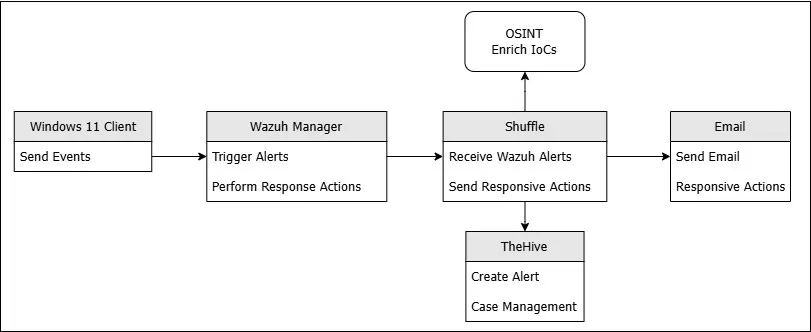
Intro
Anything to make Identification, Containment, or Eradication of a particular threat quicker is always a nice to have. The objective of this project is to achieve automation capability to defend against nefarious activities.
This project will include:
- Wazuh - for SIEM and XDR
- TheHive - for Case Management
- Shuffle - for SOAR capabilities
Brief
I’ll be setting up SOAR and integrate Wazuh, TheHive & Shuffle together. I’ll configure alerts which will be sent over to the SOAR platform and then create the same alert in TheHive for case management, while automatically emailing analysts about the details of the alert, along with automated responsive capabilities.
Sending alerts to a case management system is important because in a real-world SOC environment, we’ll want our alerts organized. In TheHive, we can create cases based on the alert, know the status of the alert, and also know who is working on the alerts.
This setup mimics a SOC environment. With emails being sent directly to an inbox to review the details of the alert, along with responsive actions attached with the email, the response time to an incident can be significantly reduced.
A manual intervention of the investigation might look something the below:
- If an IDS alert were to be generated for Cobalt Strike (Alert)
- The analyst may choose not to engage in the automatic response action and then manually begin to look at surrounding events (Triage)
- Let’s say if an user were to access a malicious domain/suspicious website prior to the alert (Event of interest)
- Additional analysis can then be performed on that domain (Research). Domain reputation tools can be utilized for passive analysis. One can also perform dynamic analysis if necessary by analyzing the domain’s behavior by accessing it
Lab diagram
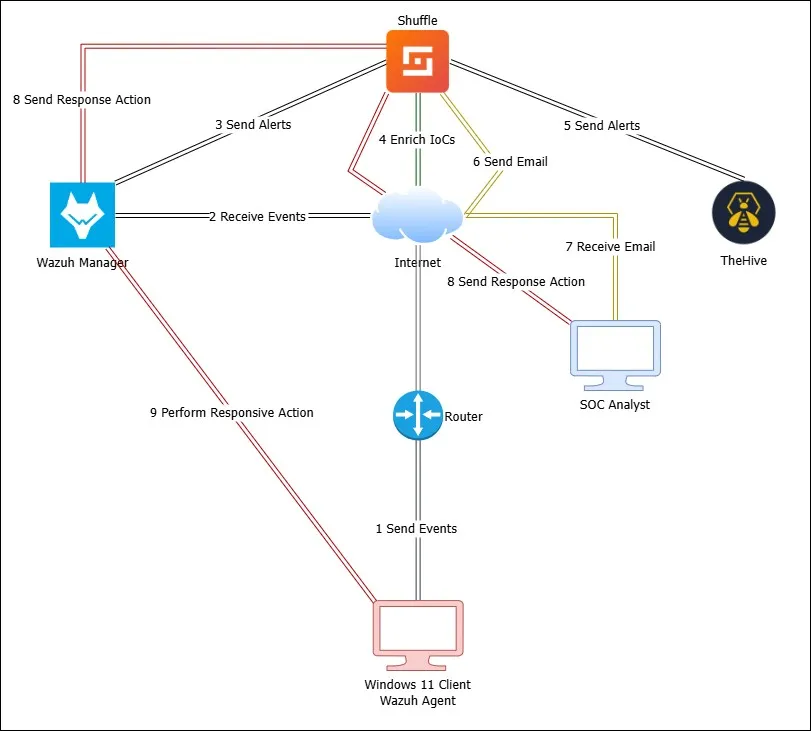
Flowchart